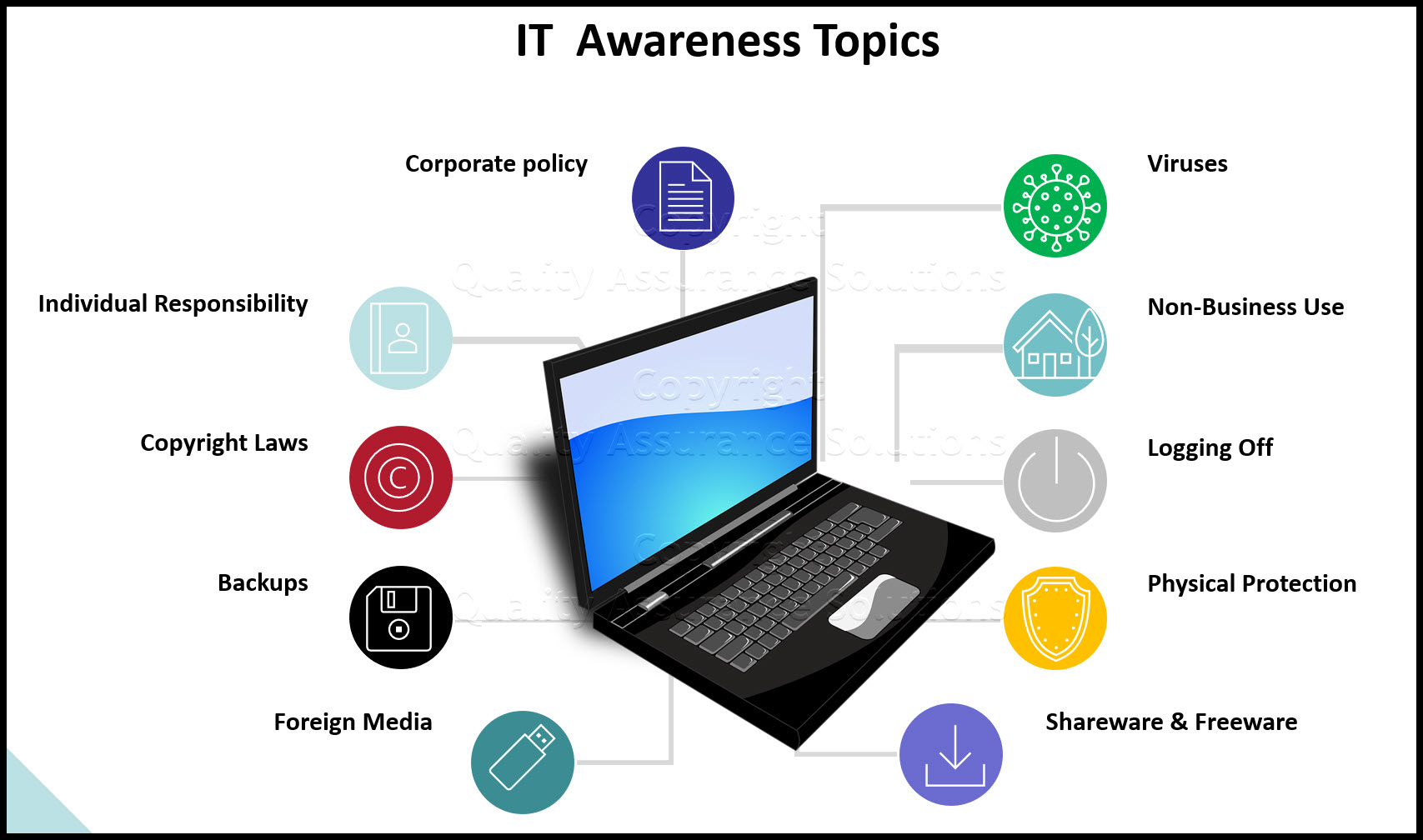
Secure Laptop Locked Privacy Policy Safety Lock And Data Protection Concept Stock Illustration - Download Image Now - iStock

Laptop Security Policy - How to create a Laptop Security Policy ? Download this Laptop Security Policy t… | Policy template, Laptop security, Information governance

![How to Build a Cyber Security Policy [5 Tips] How to Build a Cyber Security Policy [5 Tips]](https://www.soscanhelp.com/hubfs/Business%20Meeting%20Header.png)




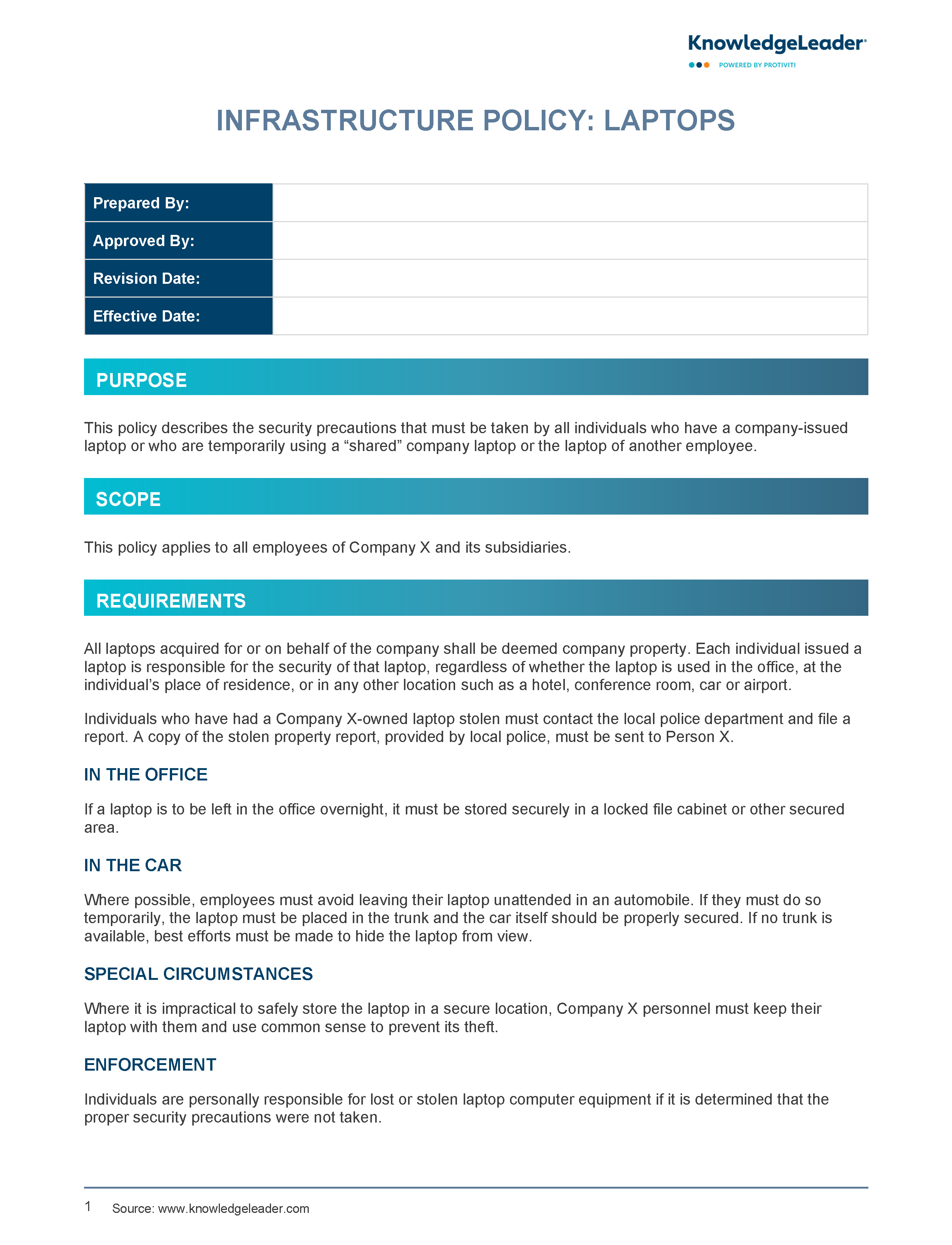



![42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab 42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab](https://templatelab.com/wp-content/uploads/2018/05/Security-Policy-12.jpg)